Azure Security Interview Questions with Answer on IAM
Azure Identity and Access Management (IAM) is a critical component of the Microsoft Azure ecosystem, designed to ensure secure access to resources and services within the cloud environment. For organizations using Azure, effective IAM practices are essential to maintaining security, ensuring compliance, and managing users, applications, and resources efficiently. Senior-level professionals in Azure IAM are expected to possess in-depth knowledge of Azure Active Directory (AD) now Microsoft Entra ID, role-based access control (RBAC), multi-factor authentication (MFA), and various other security protocols that safeguard enterprise cloud environments.
This compilation of senior-level interview questions focuses on testing a candidate’s expertise in Azure IAM, covering areas such as authentication protocols, identity management, hybrid identity, conditional access, and best practices for managing privileged access. Each question is accompanied by a detailed answer to provide insights into the essential concepts and features of Azure IAM, ensuring a comprehensive understanding of how to securely manage identities and control access in a cloud-first world.
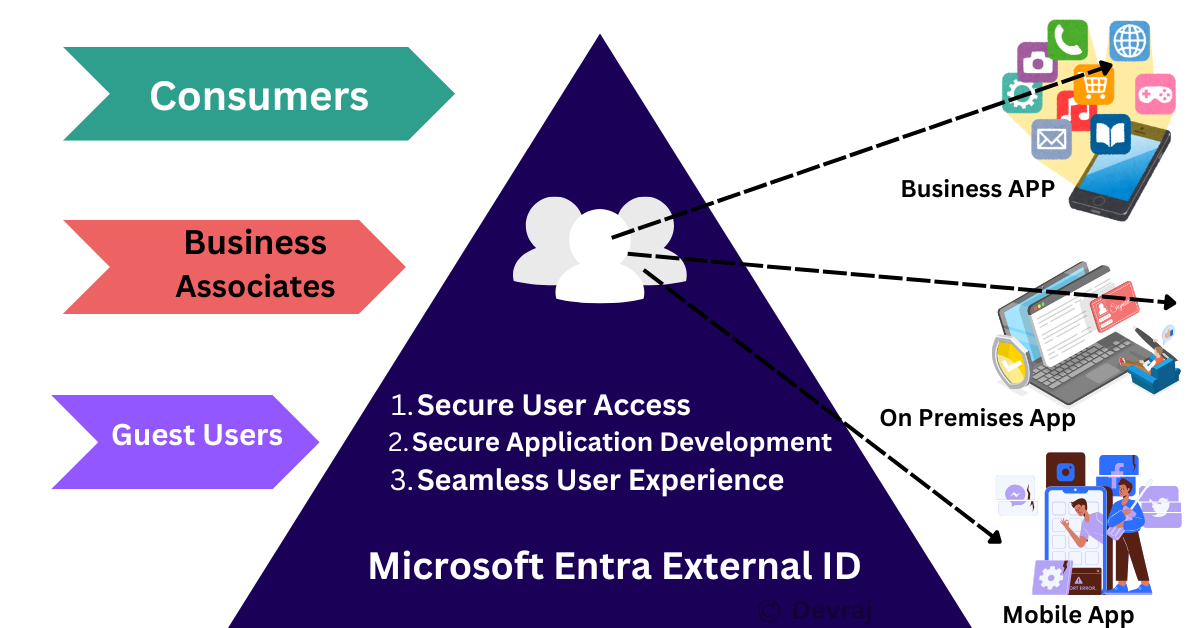
Q1. What is Microsoft Entra External ID?
Microsoft Entra External ID is a cloud-based identity and access management solution that allows organizations to securely manage external identities, such as customers, partners, or citizens, while providing seamless and customized authentication experiences. It builds on the capabilities previously offered by Azure AD B2C (Business to Consumer) and focuses on managing external user access to applications, services, and resources.
Key Features of Microsoft Entra External ID:
- Customer Identity and Access Management (CIAM): It helps organizations manage authentication and authorization for external users (consumers or partners) without compromising security.
- Customizable User Experiences: Organizations can fully customize the sign-up, sign-in, and profile management experiences, including the UI/UX to reflect their brand identity.
- Support for Multiple Identity Providers: Microsoft Entra External ID allows users to authenticate using social identity providers (such as Google, Facebook, LinkedIn), enterprise identity providers (through SAML or OpenID Connect), and local accounts (username and password, phone-based authentication).
- Scalability: It is designed to scale to millions of external users, making it suitable for large-scale applications and services.
- Advanced Security Features:
- Multi-Factor Authentication (MFA) can be enforced for added security.
- Identity Protection features like risk-based Conditional Access can be applied to detect and mitigate suspicious activities.
- Compliance and Privacy Controls: Provides robust compliance tools to help organizations adhere to privacy regulations like GDPR, ensuring secure data handling and management of external user data.
- Integration with External Applications: Microsoft Entra External ID can integrate with external, third-party applications, making it easier for developers to implement secure sign-in and identity management for consumer-facing applications.

Use Cases for Microsoft Entra External ID:
- Retail and E-commerce: Securely manage customer identities for online shopping platforms.
- Government Services: Provide secure citizen access to government portals and services.
- Healthcare: Manage patient identities while ensuring privacy and security compliance.
- Education: Provide students and faculty with access to learning platforms.
Q2. Is Microsoft Entra External ID a new name for Azure AD B2C?
Yes, Microsoft Entra External ID is the new branding for Azure AD B2C (Business to Consumer). This rebranding aligns with Microsoft’s broader strategy under the Microsoft Entra family, which focuses on comprehensive identity and access solutions. While the core functionality of enabling businesses to manage customer identities and access remains the same, the name change emphasizes Microsoft’s expansion in the identity management space.
Key Features of Microsoft Entra External ID (formerly Azure AD B2C):
- It provides identity management solutions for consumer-facing applications.
- Supports authentication through external identity providers like Google, Facebook, and Microsoft accounts, along with local accounts.
- Enables businesses to customize the user authentication experience and securely manage access for millions of consumer users.
This rebranding under the Microsoft Entra umbrella highlights the unification of identity management solutions, including Microsoft Entra ID (formerly Azure AD) and Microsoft Entra External ID, focusing on external user scenarios.
Q3. What’s the difference between external and workforce tenants?
The key difference between External and Workforce tenants in the Microsoft Entra ecosystem lies in who the users are and how their identities are managed.
Here’s a breakdown of the differences:
1. Workforce Tenant
- Purpose: Designed for managing the identities and access of employees, contractors, and internal users within an organization.
- Primary Users: Employees, contractors, vendors, and internal team members.
- Features:
- Microsoft Entra ID (formerly Azure AD) is primarily used for managing workforce identities.
- Enables secure access to internal applications, cloud services, and corporate resources.
- Supports features like Single Sign-On (SSO), Multi-Factor Authentication (MFA), Conditional Access Policies, and Privileged Identity Management (PIM).
- Often integrates with on-premises systems (via hybrid identity) to manage internal identities across different services.
- Identity governance and lifecycle management tools ensure compliance and security for internal users.
- Use Case: This is ideal for organizations that need to manage how employees and internal users access company applications and resources.
2. External Tenant
- Purpose: Tailored for managing external or guest users, such as customers, partners, and collaborators outside the organization.
- Primary Users: Customers, partners, third-party vendors, and any users who need access to specific services but are not part of the workforce.
- Features:
- Microsoft Entra External ID (formerly Azure AD B2C) is used to manage external identities.
- Focuses on managing consumer-facing authentication and access scenarios for customers or partners.
- Supports authentication using external identity providers (like Google, Facebook, Microsoft accounts) or local identities.
- Highly customizable user experience (sign-in, sign-up, profile management), allowing external-facing apps to be branded to the organization’s needs.
- Enables external collaboration through B2B (Business-to-Business) scenarios using Microsoft Entra External ID.
- Use Case: Suitable for organizations that need to manage large numbers of external users (such as customers or partners) accessing services like e-commerce platforms, government portals, or collaborative tools.
Summary of Differences:
| Aspect | Workforce Tenant | External Tenant |
|---|---|---|
| User Type | Employees, contractors, internal users | Customers, partners, external collaborators |
| Primary Purpose | Manage internal workforce access to apps | Manage external user access to apps |
| Identity Solution | Microsoft Entra ID (formerly Azure AD) | Microsoft Entra External ID (formerly B2C) |
| Authentication Methods | Supports internal identity and SSO | Supports external identities (social login) |
| Customization | Focus on secure internal collaboration | Focus on customizable user experience |
| Scale | Workforce management (typically smaller) | External user management (potentially millions of users) |
In essence, workforce tenants manage internal employees and team members, ensuring secure access to organizational resources, while external tenants are optimized for handling identities and access for external customers and partners, offering more flexibility and customization for user experiences.
Q4. What identity providers does External ID support?
Microsoft Entra External ID (formerly Azure AD B2C) supports a variety of identity providers to offer flexible authentication options for external users such as customers and partners. These providers can be categorized into three main types: Social Identity Providers, Enterprise Identity Providers, and Local Identities.
1. Social Identity Providers
These are popular external services that allow users to authenticate using their existing accounts. External ID supports:
- Google: Users can sign in using their Google accounts (Gmail).
- Facebook: Allows authentication through Facebook login.
- Microsoft Account (MSA): Users can sign in using their Microsoft account (Outlook.com, Hotmail, etc.).
- Twitter: Supports authentication via Twitter login.
- LinkedIn: Users can authenticate using their LinkedIn credentials.
These social logins are ideal for consumer-facing applications that need to simplify sign-in experiences for a large audience.
2. Enterprise Identity Providers
For scenarios involving business-to-business (B2B) collaboration, Microsoft Entra External ID supports enterprise-grade identity providers using protocols like SAML, OpenID Connect, or OAuth 2.0. Examples include:
- Azure AD / Microsoft Entra ID (Enterprise): Supports users from other Microsoft Entra tenants, allowing organizations to invite external business partners or collaborators.
- ADFS (Active Directory Federation Services): On-premises Active Directory users can authenticate via federation with ADFS.
- Any SAML 2.0-compliant provider: Allows users from organizations using SAML 2.0-based identity providers.
- Any OpenID Connect (OIDC)-compliant provider: Supports third-party identity systems or enterprise providers that use OpenID Connect.
This is useful for organizations that collaborate with partners who have their own corporate identity systems.
3. Local Identities (Username/Password)
Microsoft Entra External ID also allows businesses to create and manage local accounts for users. These local identities are based on:
- Username/Password: Users can create an account specifically for the service or application, with their own username and password.
- Phone Number (SMS-based): Users can authenticate or sign up using their mobile phone numbers, receiving verification via SMS.
- Email-based Authentication: Users can register using their email addresses and authenticate via verification emails.
This is particularly useful for organizations that need to handle custom identity requirements or provide a simple method for users who don’t want to use social or enterprise logins.
Q5. What are Identity Tokens, and how do they work in Microsoft Entra ID?
Identity Tokens in Microsoft Entra ID (formerly Azure AD) are a type of security token used in the authentication process to prove a user’s identity to a particular application. They are issued by Microsoft Entra ID as part of the OpenID Connect (OIDC) protocol and are primarily used for authentication.
How Identity Tokens Work in Microsoft Entra ID
- Authentication Flow:
- When a user tries to access a secured application, the application redirects the user to Microsoft Entra ID to authenticate.
- After successful authentication (e.g., via username/password, MFA), Microsoft Entra ID issues an Identity Token to the requesting application.
- The token contains claims about the user, such as their username, email, and any groups or roles they belong to, which the application can use to validate the user’s identity.
- Token Format:
- Identity Tokens are JSON Web Tokens (JWTs), which are compact, URL-safe tokens. These tokens are signed by Microsoft Entra ID to ensure their authenticity.
- JWTs consist of three parts:
- Header: Contains metadata about the token, such as the type of token (JWT) and the signing algorithm (e.g., RS256).
- Payload: Contains the claims (i.e., user information) such as user ID, email, and other relevant details.
- Signature: A cryptographic signature that ensures the token hasn’t been tampered with. The application can verify this signature to trust the contents of the token.
- Claims:
- The Payload of the Identity Token includes claims, which are key-value pairs that provide information about the user and authentication. Common claims in an Identity Token include:
- sub (subject): A unique identifier for the user.
- name: The full name of the user.
- email: The user’s email address.
- iat (issued at): Timestamp when the token was issued.
- exp (expiration time): Timestamp indicating when the token will expire.
- aud (audience): The identifier for the application the token is intended for.
- The Payload of the Identity Token includes claims, which are key-value pairs that provide information about the user and authentication. Common claims in an Identity Token include:
- Verification:
- The application receiving the Identity Token must verify its authenticity by checking the signature and ensuring the token was issued by a trusted Microsoft Entra ID tenant.
- It also checks the token’s expiration (
expclaim) and audience (audclaim) to ensure the token is still valid and intended for the application.
- User Information:
- Once the Identity Token is verified, the application can extract the user’s information from the claims. This information is used to authenticate the user and provide access to appropriate resources or personalize the user experience.
Example Flow for Identity Token in Microsoft Entra ID:
- A user attempts to log in to an application (e.g., a web app or mobile app).
- The app redirects the user to Microsoft Entra ID for authentication.
- The user provides their credentials (or uses other authentication methods like MFA).
- Microsoft Entra ID validates the credentials and issues an Identity Token to the app.
- The app verifies the token’s signature and checks the claims (e.g.,
sub,email). - The app grants the user access based on the authenticated identity provided by the token.
Key Points:
- Security: The tokens are signed by Microsoft Entra ID, ensuring they cannot be tampered with.
- Stateless: Identity Tokens are self-contained, meaning the app doesn’t need to make additional calls to verify the user’s identity once the token is issued.
- Short-lived: These tokens have a short lifespan (typically minutes to hours), so they expire quickly, reducing security risks.
Use Cases:
- Web and Mobile Apps: Identity Tokens are used to authenticate users in web or mobile applications without storing passwords in the application.
- SSO (Single Sign-On): They are commonly used in SSO scenarios, allowing users to authenticate once and access multiple applications.
- API Access: In combination with OAuth 2.0, Identity Tokens can be used to authenticate users before granting access to APIs or backend services.
Looking for a classroom training on Cloud Security in Kolkata click here

Cybersecurity Architect | Cloud-Native Defense | AI/ML Security | DevSecOps
With over 23 years of experience in cybersecurity, I specialize in building resilient, zero-trust digital ecosystems across multi-cloud (AWS, Azure, GCP) and Kubernetes (EKS, AKS, GKE) environments. My journey began in network security—firewalls, IDS/IPS—and expanded into Linux/Windows hardening, IAM, and DevSecOps automation using Terraform, GitLab CI/CD, and policy-as-code tools like OPA and Checkov.
Today, my focus is on securing AI/ML adoption through MLSecOps, protecting models from adversarial attacks with tools like Robust Intelligence and Microsoft Counterfit. I integrate AISecOps for threat detection (Darktrace, Microsoft Security Copilot) and automate incident response with forensics-driven workflows (Elastic SIEM, TheHive).
Whether it’s hardening cloud-native stacks, embedding security into CI/CD pipelines, or safeguarding AI systems, I bridge the gap between security and innovation—ensuring defense scales with speed.
Let’s connect and discuss the future of secure, intelligent infrastructure.